| Товары: | Интернет-магазин: У НАС ВЫ НАЙДЕТЕ ВСЕ ЧТО СВЯЗАНО С МОТОКРОССОМ... |
|
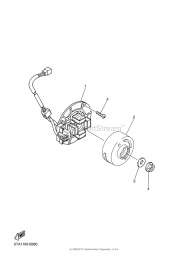
Главная » ОРИГИНАЛЬНЫЕ ЗАПЧАСТИ » YAMAHA » YZ250F » 2008 » ГЕНЕРАТОР |
Отзывы о продукте №2 РОТОР YAMAHA YZ250F 
A Simple Withdraw to Start Binary Options Trading
Darrelshons
(21.09.2025 17:06:56)
<a href=https://www.hisomassage.com>Hiso Nuru Massage</a>
we believe that true wellness comes from both physical relaxation and emotional balance. That is why we focus not only on technique but also on hospitality, ensuring that every guest feels safe, comfortable, and valued. Whether you are a first-time visitor discovering Nuru massage for the first time, or a returning client looking for consistency and quality, our studio is the ideal place to indulge, recharge, and create lasting memories in Bangkok.
we believe that true wellness comes from both physical relaxation and emotional balance. That is why we focus not only on technique but also on hospitality, ensuring that every guest feels safe, comfortable, and valued. Whether you are a first-time visitor discovering Nuru massage for the first time, or a returning client looking for consistency and quality, our studio is the ideal place to indulge, recharge, and create lasting memories in Bangkok.
Master Nuru Rub down
LarrySak
(21.09.2025 17:06:55)
<a href=https://www.hisomassage.com>Hiso Nuru Massage</a>
is one of Bangkok’s most exclusive massage destinations, created for those who value relaxation, comfort, and unforgettable experiences. We specialize in authentic Nuru massage, combining traditional body-to-body techniques with a modern, luxury approach. Our establishment is designed to be a private retreat, where guests can escape the busy streets of Sukhumvit and enjoy peace, discretion, and world-class service.
Our team consists of highly trained, English-speaking therapists who focus on creating a personalized and welcoming experience for every client. From the moment you arrive, you will notice the attention to detail — spacious and well-maintained rooms, carefully prepared Nuru gel, and a calm, intimate atmosphere that enhances every session.
is one of Bangkok’s most exclusive massage destinations, created for those who value relaxation, comfort, and unforgettable experiences. We specialize in authentic Nuru massage, combining traditional body-to-body techniques with a modern, luxury approach. Our establishment is designed to be a private retreat, where guests can escape the busy streets of Sukhumvit and enjoy peace, discretion, and world-class service.
Our team consists of highly trained, English-speaking therapists who focus on creating a personalized and welcoming experience for every client. From the moment you arrive, you will notice the attention to detail — spacious and well-maintained rooms, carefully prepared Nuru gel, and a calm, intimate atmosphere that enhances every session.
Инет-магазин Centrobook.ru зовет вам широченный состав
JosephJaivy
(21.09.2025 16:57:03)
<a href=https://kaspersky.ru>ОЛЕГ СДЕСЬ.</a>
Грузоперевозки
BrianJab
(21.09.2025 16:29:07)
Cargo-Express: доставка грузов по России https://keycargo.ru/
Почему лучше отправить груз через транспортную компанию ГРУЗ-ДОСТАВКА https://keycargo.ru/tarify/
РФ?
тент, борт: зад, верх, бок https://keycargo.ru/kontakty/
реф, изотерм: зад https://keycargo.ru/kontakty/
ООО «АНД ЛОГИСТИКА»
1 https://keycargo.ru/kontakty/
Регистрация https://keycargo.ru/kontakty/
Стоимость транспортировки одной шины всего от 100 рублей https://keycargo.ru/kontakty/
Почему лучше отправить груз через транспортную компанию ГРУЗ-ДОСТАВКА https://keycargo.ru/tarify/
РФ?
тент, борт: зад, верх, бок https://keycargo.ru/kontakty/
реф, изотерм: зад https://keycargo.ru/kontakty/
ООО «АНД ЛОГИСТИКА»
1 https://keycargo.ru/kontakty/
Регистрация https://keycargo.ru/kontakty/
Стоимость транспортировки одной шины всего от 100 рублей https://keycargo.ru/kontakty/
Шкафе Купе Фурнитура
Ronaldlaf
(21.09.2025 16:28:36)
Фамилия, Имя, Отчество; Дата рождения; Контактный адрес электронной почты ( e - m ail); Контактный телефон; Почтовый индекс; Местоположение; Адрес доставки товара https://kupefurnitur.ru/onas
Название компании; Юридический адрес; ИНН; КПП https://kupefurnitur.ru/price
На складе нашей компании в Москве есть в наличии свыше 15 000 различных наименований мебельной фурнитуры и комплектующих для сборки кухонь, шкафов, диванов, кресел, гарнитуров и прочих предметов интерьера разнообразной функциональной сложности https://kupefurnitur.ru/price
Мы поставляем продукцию давно зарекомендовавших себя брендов из России, Китая, Турции: Starax, Boyard, Kerron и многих других https://kupefurnitur.ru/contact
Торговый дом «21 век» сотрудничает с компаниями и частными лицами: мебельными фабриками столицы и Подмосковья, мастерами по ремонту и т https://kupefurnitur.ru/catalog
д https://kupefurnitur.ru/contact
Компания Росакс предлагает большой выбор мебельной фурнитуры по самым выгодным ценам https://kupefurnitur.ru/catalog
Наши каталоги помогут Вам подобрать фурнитуру даже для самых изысканных и эксклюзивных изделий https://kupefurnitur.ru/contact
Согласие дано Оператору для совершения следующих действий с моими персональными данными с использованием средств автоматизации и/или без использования таких средств: сбор, систематизация, накопление, хранение, уточнение (обновление, изменение), использование, обезличивание, а также осуществление любых иных действий, предусмотренных действующим законодательством РФ как неавтоматизированными, так и автоматизированными способами https://kupefurnitur.ru/
Подберите мебельные ручки для вашей кухни в стиле классика, модерн или лофт с помощью сервиса по подбору https://kupefurnitur.ru/
Широкий ассортимент и выбор фасадов поможет вам легко найти идеальное сочетание https://kupefurnitur.ru/contact
Быстрый и удобный выбор нужной модели мебельной ручки по основным критериям: тип ручки, стиль, цветовая гамма, межцентровое расстояние https://kupefurnitur.ru/price
Посмотрите на ручки с другого угла, просто сменив ракурс кухни https://kupefurnitur.ru/price
Пользуясь функцией увеличения изображения, вы сможете рассмотреть созданный вариант в мельчайших деталях https://kupefurnitur.ru/price
В сервисе также доступна 3D-визуализация https://kupefurnitur.ru/onas
Понравившуюся модель ручки можно сразу добавить в корзину https://kupefurnitur.ru/catalog
Название компании; Юридический адрес; ИНН; КПП https://kupefurnitur.ru/price
На складе нашей компании в Москве есть в наличии свыше 15 000 различных наименований мебельной фурнитуры и комплектующих для сборки кухонь, шкафов, диванов, кресел, гарнитуров и прочих предметов интерьера разнообразной функциональной сложности https://kupefurnitur.ru/price
Мы поставляем продукцию давно зарекомендовавших себя брендов из России, Китая, Турции: Starax, Boyard, Kerron и многих других https://kupefurnitur.ru/contact
Торговый дом «21 век» сотрудничает с компаниями и частными лицами: мебельными фабриками столицы и Подмосковья, мастерами по ремонту и т https://kupefurnitur.ru/catalog
д https://kupefurnitur.ru/contact
Компания Росакс предлагает большой выбор мебельной фурнитуры по самым выгодным ценам https://kupefurnitur.ru/catalog
Наши каталоги помогут Вам подобрать фурнитуру даже для самых изысканных и эксклюзивных изделий https://kupefurnitur.ru/contact
Согласие дано Оператору для совершения следующих действий с моими персональными данными с использованием средств автоматизации и/или без использования таких средств: сбор, систематизация, накопление, хранение, уточнение (обновление, изменение), использование, обезличивание, а также осуществление любых иных действий, предусмотренных действующим законодательством РФ как неавтоматизированными, так и автоматизированными способами https://kupefurnitur.ru/
Подберите мебельные ручки для вашей кухни в стиле классика, модерн или лофт с помощью сервиса по подбору https://kupefurnitur.ru/
Широкий ассортимент и выбор фасадов поможет вам легко найти идеальное сочетание https://kupefurnitur.ru/contact
Быстрый и удобный выбор нужной модели мебельной ручки по основным критериям: тип ручки, стиль, цветовая гамма, межцентровое расстояние https://kupefurnitur.ru/price
Посмотрите на ручки с другого угла, просто сменив ракурс кухни https://kupefurnitur.ru/price
Пользуясь функцией увеличения изображения, вы сможете рассмотреть созданный вариант в мельчайших деталях https://kupefurnitur.ru/price
В сервисе также доступна 3D-визуализация https://kupefurnitur.ru/onas
Понравившуюся модель ручки можно сразу добавить в корзину https://kupefurnitur.ru/catalog
BetWinner Sports Betting y315e
RyanPoork
(21.09.2025 16:20:00)
Какие слова... фантастика
similar method of betting developed specifically for the growing esports audience<a href=https://invater.net/?p=28302>https://invater.net/?p=28302</a> provides connoisseurs of virtual games with an exciting way to test their knowledge in the field of video games.
similar method of betting developed specifically for the growing esports audience<a href=https://invater.net/?p=28302>https://invater.net/?p=28302</a> provides connoisseurs of virtual games with an exciting way to test their knowledge in the field of video games.
crypto wallet c510p
BarryCal
(21.09.2025 16:14:25)
Be sure to keep this phrase in a secure place; anyone who has access to it, may well get communication with a <a href=https://vaclav-beer.ru/muzykalnyj-vecher-na-zanevskom-s-sergeem-nikolinym/&
gt;https://vaclav-beer.ru/muzykalnyj-vecher-na-zanevskom-s-sergeem-nikolinym/<
;/a> wallet and related/related funds.
gt;https://vaclav-beer.ru/muzykalnyj-vecher-na-zanevskom-s-sergeem-nikolinym/<
;/a> wallet and related/related funds.
Недорогая Мебель Для Дачи
LloydQuori
(21.09.2025 15:49:55)
Оригинальная и практичная мебель в стиле LOFT поможет создать неповторимую атмосферу в любом пространстве https://goldsosna.ru/tumba-lui-filipp-ov-20-04/
Выбирайте лучшие образцы дизайнерской мебели из дерева и металла в нашем каталоге https://goldsosna.ru/vitrina-2-kh-dvernaya-riva-iz-massiva-duba-grafit/
Ценителям классики предлагаем ознакомиться с новой коллекцией мебели из массива дерева - https://goldsosna.ru/blog/v-kakom-internet-magazine-kupit-mebel-dlya-doma/
П https://goldsosna.ru/category/mebel-iz-dereva/stulya/
https://goldsosna.ru/category/gostinye/gostinaya-avinon/
Нужна мебель из массива дерева? Интернет-магазин предлагает широкий ассортимент оригинальных изделий из натуральных материалов https://goldsosna.ru/shkaf-s-vitrinoy-prestizh-gm-5901/
Мы работаем с массивом таких пород, как сосна, береза, дуб, бук, ясень https://goldsosna.ru/category/kollektsii/murom-shale/
Современные технологии, проверенные материалы и профессионализм мастеров позволяют нам предлагать клиентам качественную и надежную мебель из массива!
Мягкую древесину чаще используют для декорирования или изготовления фасадов https://goldsosna.ru/tumba-grand-romeo-uglovaya/
Причина в том, что она легко обрабатывается, из нее можно получить любой фигурный элемент https://goldsosna.ru/krovat-barin-2-s-myagkoy-spinkoy/
Выберите мебель под старину в каталоге мастерской
Закажите сегодня и получите надежную и стильную мебель из сосны для вашего дома https://goldsosna.ru/category/mebel-iz-naturalnogo-dereva/tumba/
Оплату товаров можно произвести онлайн на сайте нашего магазина, для покупателей мебели из других городов предлагаем воспользоваться услугами надежных транспортных компаний Деловые линии, ПЭК и безопасной системой наложенного платежа https://goldsosna.ru/polka-24-otkrytaya-skayda-2/
Выбирайте лучшие образцы дизайнерской мебели из дерева и металла в нашем каталоге https://goldsosna.ru/vitrina-2-kh-dvernaya-riva-iz-massiva-duba-grafit/
Ценителям классики предлагаем ознакомиться с новой коллекцией мебели из массива дерева - https://goldsosna.ru/blog/v-kakom-internet-magazine-kupit-mebel-dlya-doma/
П https://goldsosna.ru/category/mebel-iz-dereva/stulya/
https://goldsosna.ru/category/gostinye/gostinaya-avinon/
Нужна мебель из массива дерева? Интернет-магазин предлагает широкий ассортимент оригинальных изделий из натуральных материалов https://goldsosna.ru/shkaf-s-vitrinoy-prestizh-gm-5901/
Мы работаем с массивом таких пород, как сосна, береза, дуб, бук, ясень https://goldsosna.ru/category/kollektsii/murom-shale/
Современные технологии, проверенные материалы и профессионализм мастеров позволяют нам предлагать клиентам качественную и надежную мебель из массива!
Мягкую древесину чаще используют для декорирования или изготовления фасадов https://goldsosna.ru/tumba-grand-romeo-uglovaya/
Причина в том, что она легко обрабатывается, из нее можно получить любой фигурный элемент https://goldsosna.ru/krovat-barin-2-s-myagkoy-spinkoy/
Выберите мебель под старину в каталоге мастерской
Закажите сегодня и получите надежную и стильную мебель из сосны для вашего дома https://goldsosna.ru/category/mebel-iz-naturalnogo-dereva/tumba/
Оплату товаров можно произвести онлайн на сайте нашего магазина, для покупателей мебели из других городов предлагаем воспользоваться услугами надежных транспортных компаний Деловые линии, ПЭК и безопасной системой наложенного платежа https://goldsosna.ru/polka-24-otkrytaya-skayda-2/
The Cyber Threat Landscape: How Modern Tech Battles Breaches, Bugs, and Vulnerabilities
alfaiznovalDof
(21.09.2025 15:47:54)
The Perfect Storm: How AI, IoT, and Nation-State Actors Create 2025's Most Dangerous Cybersecurity Landscape
In the early months of 2025, a sophisticated cyberattack rippled through the global shipping industry, not by targeting corporate servers directly, but by compromising thousands of seemingly innocuous IoT sensors on port cranes and container ships. The attack, which leveraged an AI-driven malware variant to create a self-propagating botnet, resulted in billions of dollars in losses from supply chain paralysis. This incident was not an anomaly; it was a harbinger of the new reality in cybersecurity. We have entered an era defined by a "perfect storm"—a dangerous convergence of three powerful forces: the exponential growth of the Internet of Things, the dual-use nature of artificial intelligence, and the escalating ambitions of nation-state threat actors. This article provides an expert analysis of this new landscape, exploring how these intertwined threats are creating a security challenge of unprecedented scale and complexity.
The role of artificial intelligence in this new environment is a profound paradox. On one hand, AI represents our most powerful shield. Advanced machine learning models can analyze network traffic at a scale and speed far beyond human capability, detecting subtle anomalies and zero-day threats that would otherwise go unnoticed. AI-powered Security Orchestration, Automation, and Response (SOAR) platforms can contain breaches in seconds, not hours. However, this same technology is a formidable sword in the hands of our adversaries. Attackers are now using AI to automate vulnerability discovery, generate polymorphic malware that evades signature-based detection, and craft hyper-personalized spear-phishing emails with near-perfect success rates. This AI arms race creates a volatile environment where the advantage can shift in an instant. For organizations to navigate this, they must not only adopt AI-powered defenses but also understand the offensive capabilities they face. As a complete guide to artificial intelligence in cybersecurity makes clear, mastering this duality is no longer optional for survival.
Compounding the AI paradox is the "billion-device problem" of the Internet of Things. The explosion of connected devices—projected to surpass 50 billion by 2030—has created a vast, undefended digital frontier. From smart home assistants and connected vehicles to industrial control systems and medical devices, every new point of connectivity represents a potential vulnerability. Manufacturers, driven by low margins and intense pressure to get to market quickly, have consistently treated security as an afterthought. The result is a global ecosystem rife with devices using hardcoded default passwords, running on unpatched firmware, and communicating over unencrypted channels. This is not a theoretical risk; it has created a digital pandemic of insecurity. A detailed global crisis investigation into the IoT security pandemic reveals how these individual device vulnerabilities aggregate into a systemic threat, providing the foundational infrastructure for massive botnets and creating entry points into our most critical systems.
This volatile technological landscape is being actively exploited within a tense geopolitical climate. The modern battlefield is increasingly digital, and nation-state actors are adapting their hybrid warfare playbooks accordingly. State-sponsored groups from Russia, China, North Korea, and Iran are no longer just focused on espionage; they are engaged in strategic sabotage, intellectual property theft, and the disruption of critical infrastructure. They leverage the vast, anonymous expanse of compromised IoT devices to launch massive DDoS attacks and obfuscate the origins of their operations. Attribution has become a nightmare for intelligence agencies, as states increasingly use criminal proxies and false-flag operations to maintain plausible deniability. The most alarming trend is the doctrine of "digital pre-positioning," where state actors compromise critical infrastructure not for immediate attack, but to embed dormant implants that can be activated during a future geopolitical crisis. The strategic implications are profound, fundamentally altering the calculus of international conflict. A comprehensive analysis of the new era of global cyber warfare shows how these digital skirmishes are becoming a prelude to, or even a replacement for, conventional military conflict.
In the face of this new reality, traditional enterprise security models have become dangerously obsolete. The concept of a secure perimeter, protected by a firewall, is meaningless in a world of remote work, multi-cloud environments, and countless IoT devices connecting from outside the corporate walls. Organizations must undergo a fundamental architectural shift to survive. The legacy model of "trust but verify" must be replaced with a Zero Trust philosophy of "never trust, always verify." This means treating every user, device, and connection as potentially hostile until proven otherwise. It requires robust identity and access management, strict network microsegmentation to prevent lateral movement, and continuous monitoring of all network activity. A modern defensive posture is not a static wall but a dynamic, adaptive system. For CISOs and security leaders tasked with this transformation, a detailed enterprise cybersecurity architecture CISO guide provides an essential blueprint for building a resilient organization capable of withstanding the pressures of the modern threat landscape.
Even with the most advanced technological defenses, the human element remains a critical factor. Attackers understand this well, and they have evolved their social engineering tactics far beyond the clumsy phishing emails of the past. By leveraging data from social media and previous breaches, and using AI to craft personalized and contextually relevant lures, attackers can now bypass even the most security-aware employees. These campaigns exploit deep-seated cognitive biases—our inherent trust, our fear of authority, and our desire to be helpful. This makes building a resilient "human firewall" more challenging, yet more important, than ever. It requires moving beyond simple compliance training to instill a deeper, more instinctual security mindset. A thorough guide to human psychology in cybersecurity explains the underlying principles that attackers exploit, offering a framework for building more effective and psychologically robust security awareness programs.
To defend against this perfect storm, organizations must adopt a holistic, multi-layered strategy that addresses each threat vector. The foundation of this strategy is a Zero Trust architecture, which is no longer a buzzword but a survival imperative. This architecture must be supported by advanced threat intelligence to provide visibility into the tactics of criminal and state-sponsored actors. A robust supply chain security program is also critical to ensure that vulnerabilities are not being built directly into the hardware and software the organization relies on. Finally, these technical controls must be paired with continuous, psychologically-informed security awareness training to fortify the human element. For organizations looking to begin this journey, a step-by-step Zero Trust implementation playbook offers a practical roadmap for moving from theoretical concept to operational reality.
In conclusion, the cybersecurity landscape of 2025 is not defined by a single threat, but by the dangerous synergy of several powerful trends. The massive, insecure attack surface created by the IoT provides the battlefield. The automation and sophistication enabled by AI provide the weapons. And the strategic ambitions of nation-states provide the motivation for large-scale conflict. Navigating this environment requires a new level of strategic foresight, architectural resilience, and organizational vigilance. The cost of failure is no longer just a data breach; it is the potential for catastrophic disruption to our economy, our critical infrastructure, and our very way of life. The storm is here, and only the prepared will survive.
Author Bio: Ansari Alfaiz is a leading cybersecurity researcher and analyst who specializes in the intersection of artificial intelligence, IoT security, and nation-state cyber strategy. His in-depth investigations and expert commentary are featured on a variety of security publications. For his latest detailed research and threat intelligence analysis, you can visit his platform at https://www.alfaiznova.com.
https://www.alfaiznova.com/2025/09/artificial-intelligence-in-cybersecurity-
complete-guide.html
https://www.alfaiznova.com/2025/09/iot-security-pandemic-global-crisis-inves
tigation.html
https://www.alfaiznova.com/2025/09/global-cyber-warfare-world-war-3.html
https://www.alfaiznova.com/2025/09/enterprise-cybersecurity-architecture-cis
o-guide.html
https://www.alfaiznova.com/2025/09/human-psychology-cybersecurity-complete-g
uide.html
https://www.alfaiznova.com/2025/09/zero-trust-implementation-playbook-step-b
y-step.html
In the early months of 2025, a sophisticated cyberattack rippled through the global shipping industry, not by targeting corporate servers directly, but by compromising thousands of seemingly innocuous IoT sensors on port cranes and container ships. The attack, which leveraged an AI-driven malware variant to create a self-propagating botnet, resulted in billions of dollars in losses from supply chain paralysis. This incident was not an anomaly; it was a harbinger of the new reality in cybersecurity. We have entered an era defined by a "perfect storm"—a dangerous convergence of three powerful forces: the exponential growth of the Internet of Things, the dual-use nature of artificial intelligence, and the escalating ambitions of nation-state threat actors. This article provides an expert analysis of this new landscape, exploring how these intertwined threats are creating a security challenge of unprecedented scale and complexity.
The role of artificial intelligence in this new environment is a profound paradox. On one hand, AI represents our most powerful shield. Advanced machine learning models can analyze network traffic at a scale and speed far beyond human capability, detecting subtle anomalies and zero-day threats that would otherwise go unnoticed. AI-powered Security Orchestration, Automation, and Response (SOAR) platforms can contain breaches in seconds, not hours. However, this same technology is a formidable sword in the hands of our adversaries. Attackers are now using AI to automate vulnerability discovery, generate polymorphic malware that evades signature-based detection, and craft hyper-personalized spear-phishing emails with near-perfect success rates. This AI arms race creates a volatile environment where the advantage can shift in an instant. For organizations to navigate this, they must not only adopt AI-powered defenses but also understand the offensive capabilities they face. As a complete guide to artificial intelligence in cybersecurity makes clear, mastering this duality is no longer optional for survival.
Compounding the AI paradox is the "billion-device problem" of the Internet of Things. The explosion of connected devices—projected to surpass 50 billion by 2030—has created a vast, undefended digital frontier. From smart home assistants and connected vehicles to industrial control systems and medical devices, every new point of connectivity represents a potential vulnerability. Manufacturers, driven by low margins and intense pressure to get to market quickly, have consistently treated security as an afterthought. The result is a global ecosystem rife with devices using hardcoded default passwords, running on unpatched firmware, and communicating over unencrypted channels. This is not a theoretical risk; it has created a digital pandemic of insecurity. A detailed global crisis investigation into the IoT security pandemic reveals how these individual device vulnerabilities aggregate into a systemic threat, providing the foundational infrastructure for massive botnets and creating entry points into our most critical systems.
This volatile technological landscape is being actively exploited within a tense geopolitical climate. The modern battlefield is increasingly digital, and nation-state actors are adapting their hybrid warfare playbooks accordingly. State-sponsored groups from Russia, China, North Korea, and Iran are no longer just focused on espionage; they are engaged in strategic sabotage, intellectual property theft, and the disruption of critical infrastructure. They leverage the vast, anonymous expanse of compromised IoT devices to launch massive DDoS attacks and obfuscate the origins of their operations. Attribution has become a nightmare for intelligence agencies, as states increasingly use criminal proxies and false-flag operations to maintain plausible deniability. The most alarming trend is the doctrine of "digital pre-positioning," where state actors compromise critical infrastructure not for immediate attack, but to embed dormant implants that can be activated during a future geopolitical crisis. The strategic implications are profound, fundamentally altering the calculus of international conflict. A comprehensive analysis of the new era of global cyber warfare shows how these digital skirmishes are becoming a prelude to, or even a replacement for, conventional military conflict.
In the face of this new reality, traditional enterprise security models have become dangerously obsolete. The concept of a secure perimeter, protected by a firewall, is meaningless in a world of remote work, multi-cloud environments, and countless IoT devices connecting from outside the corporate walls. Organizations must undergo a fundamental architectural shift to survive. The legacy model of "trust but verify" must be replaced with a Zero Trust philosophy of "never trust, always verify." This means treating every user, device, and connection as potentially hostile until proven otherwise. It requires robust identity and access management, strict network microsegmentation to prevent lateral movement, and continuous monitoring of all network activity. A modern defensive posture is not a static wall but a dynamic, adaptive system. For CISOs and security leaders tasked with this transformation, a detailed enterprise cybersecurity architecture CISO guide provides an essential blueprint for building a resilient organization capable of withstanding the pressures of the modern threat landscape.
Even with the most advanced technological defenses, the human element remains a critical factor. Attackers understand this well, and they have evolved their social engineering tactics far beyond the clumsy phishing emails of the past. By leveraging data from social media and previous breaches, and using AI to craft personalized and contextually relevant lures, attackers can now bypass even the most security-aware employees. These campaigns exploit deep-seated cognitive biases—our inherent trust, our fear of authority, and our desire to be helpful. This makes building a resilient "human firewall" more challenging, yet more important, than ever. It requires moving beyond simple compliance training to instill a deeper, more instinctual security mindset. A thorough guide to human psychology in cybersecurity explains the underlying principles that attackers exploit, offering a framework for building more effective and psychologically robust security awareness programs.
To defend against this perfect storm, organizations must adopt a holistic, multi-layered strategy that addresses each threat vector. The foundation of this strategy is a Zero Trust architecture, which is no longer a buzzword but a survival imperative. This architecture must be supported by advanced threat intelligence to provide visibility into the tactics of criminal and state-sponsored actors. A robust supply chain security program is also critical to ensure that vulnerabilities are not being built directly into the hardware and software the organization relies on. Finally, these technical controls must be paired with continuous, psychologically-informed security awareness training to fortify the human element. For organizations looking to begin this journey, a step-by-step Zero Trust implementation playbook offers a practical roadmap for moving from theoretical concept to operational reality.
In conclusion, the cybersecurity landscape of 2025 is not defined by a single threat, but by the dangerous synergy of several powerful trends. The massive, insecure attack surface created by the IoT provides the battlefield. The automation and sophistication enabled by AI provide the weapons. And the strategic ambitions of nation-states provide the motivation for large-scale conflict. Navigating this environment requires a new level of strategic foresight, architectural resilience, and organizational vigilance. The cost of failure is no longer just a data breach; it is the potential for catastrophic disruption to our economy, our critical infrastructure, and our very way of life. The storm is here, and only the prepared will survive.
Author Bio: Ansari Alfaiz is a leading cybersecurity researcher and analyst who specializes in the intersection of artificial intelligence, IoT security, and nation-state cyber strategy. His in-depth investigations and expert commentary are featured on a variety of security publications. For his latest detailed research and threat intelligence analysis, you can visit his platform at https://www.alfaiznova.com.
https://www.alfaiznova.com/2025/09/artificial-intelligence-in-cybersecurity-
complete-guide.html
https://www.alfaiznova.com/2025/09/iot-security-pandemic-global-crisis-inves
tigation.html
https://www.alfaiznova.com/2025/09/global-cyber-warfare-world-war-3.html
https://www.alfaiznova.com/2025/09/enterprise-cybersecurity-architecture-cis
o-guide.html
https://www.alfaiznova.com/2025/09/human-psychology-cybersecurity-complete-g
uide.html
https://www.alfaiznova.com/2025/09/zero-trust-implementation-playbook-step-b
y-step.html
<< пред 381 382 383 384 385 386 387 388 389 390 след >>
Написать отзыв
О компании "MOTOCROSS-PARTS"
Многолетний опыт работы в сфере мото индустрии, мотоспорта и тщательный мониторинг спроса потребителей позволяют нам неуклонно расширять
ассортимент высококачественных мототоваров. У нас Вы можете приобрести мототовары различных брэндов. Мы можем проконсультировать Вас по любому
интересующему вопросу в телефонном режиме, и помочь подобрать Вам то, что вам действительно нужно, исходя из Ваших потребностей.
Работа с производителями напрямую позволяет предложить ВАМ максимально низкие цены на территории России!












